Segment your home network today!
The age of IoT (Internet of Things) is upon us, and it poses a real challenge to the security of our home networks. This post will look at some practical approaches you can take to isolate untrustworthy devices from the rest of your home network.
10 min read
·
By Øystein Grande Jaren
·
December 14, 2021

What will you do if you wake up one morning to find that your new, smart coffee maker has been hijacked by a devious hacker? Maybe you don't get any coffee that morning, unless you pay a Bitcoin in ransom. Or perhaps the hacker does not care about coffee at all, but merely uses your all too vulnerable coffee maker as an access port to your network, and before you know it all hard drives in your house have been encrypted.
One thing is for certain: You will start thinking about how you could have prevented this travesty. The obvious answer is that you should never have connected your coffee maker to the Internet. (Why would you? Seriously?) But it seems we can't avoid the temptation to make ever more of our various devices "smart". The age of IoT (Internet of Things) is truly upon us, and while many uses of IoT technology have questionable value at best, it is undeniable that ubiquitous network and/or Internet connectivity creates possibilities which were unimaginable just a few decades ago. So whether the device that you can't live without is a smart coffee maker, smart light bulb, smart thermostat or a smart toilet (yes, that's a thing), the value-add comes at a price. Most IoT devices, especially cheap ones, run flaky software built around an outdated version of the Linux kernel riddled with security holes. Most of them will never be updated.
So what can you do, in your own home, to prevent these devices from posing a threat to the rest of your network? To understand this, we will now look at how your router actually protects the network from unwanted traffic from the outside, and why this protection is not sufficient in the age of IoT. We will then look at three different approaches you can take to split up your network and keep the insecure stuff isolated from the rest.
First line of defence: Network Address Translation (NAT)
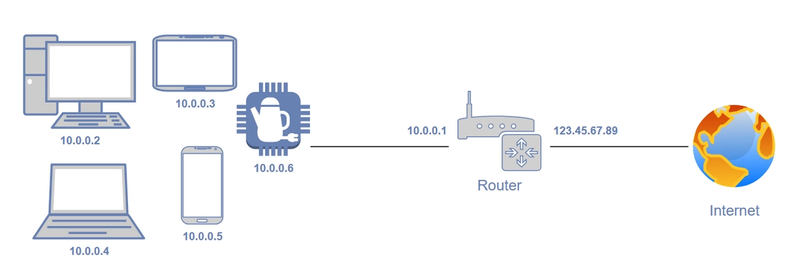
All home routers have a kind of firewall, in the sense that they block all unexpected traffic from the outside. All devices on the local network have a local IP address (typically in the 192.168.x.x space or the 10.x.x.x space). These addresses are not globally routable; packets destined for these addresses simply cannot traverse the Internet. However this does not prevent devices inside the local network from contacting addresses on the global Internet. The router keeps track of all outbound connections initiated from addresses on the local network, making sure related packets from the outside are forwarded to the correct local address. Any packets from the outside which cannot be associated with a recent request from the inside are dropped by the router. For more details on how this works, see this Wikipedia article.
This is all well and good, so long as you can trust the integrity of all the devices on your network, and that the servers they communicate with are all perfectly well-behaved Internet citizens, kept up-to-date and secure at all times. This is of course a pipe dream. If just one of those servers is compromised (or outright malicious from the start), the route to taking control of the IoT device with which it communicates is short. The device can be made part of a large globally spanning botnet and used to launch DDoS attacks against critical infrastructure anywhere in the world. If the device has some processing power, it may be put to work mining cryptocurrency. Or it may simply be used as an entry point, and a malicious software suite may be used to look for known vulnerabilites in other devices on your network, which are promptly taken control of in a similar manner.
Limiting the damage potential: Network segmentation
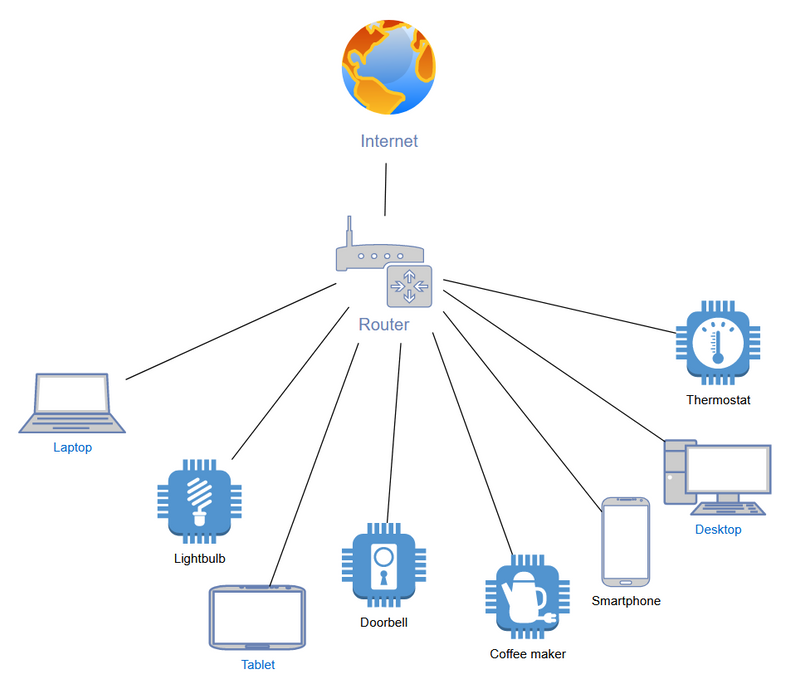
The above image shows a typical home network, with all devices connected in a flat network structure.
To limit the damage potential of a compromised device, you should split up your network, isolating all devices you do not fully trust on their own IoT network, and keeping trusted devices on the main network. A trusted device is typically a computer, tablet or mobile phone which receives frequent and timely security updates, and whose vendor has a track record of decent security. (Note that this rules out most Android phones older than three years, but that is a story for another time.)
We will now look at three different approaches you can take to segment your network.
Multiple routers
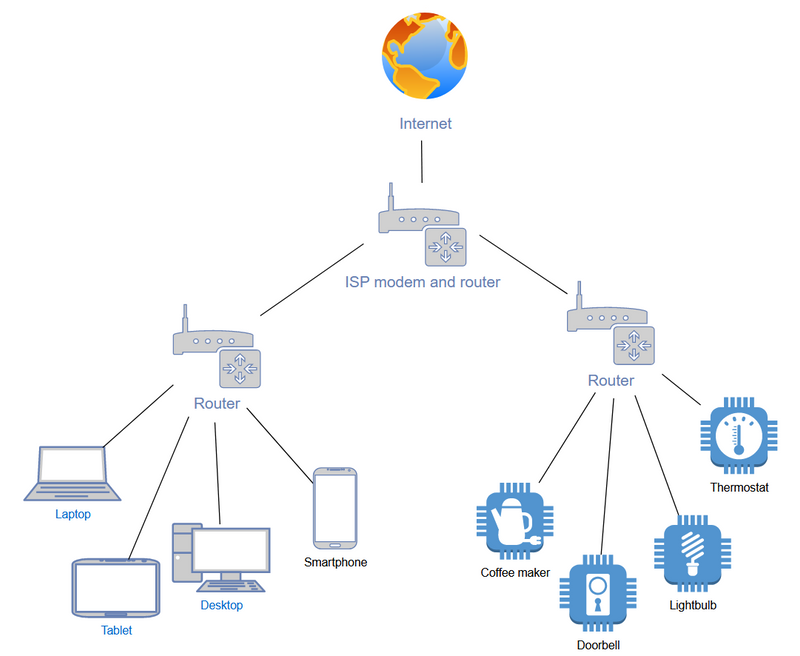
The most obvious solution is to use two different routers to create two physically separate networks. To do this properly you actually need three routers: The router provided by your ISP (Internet Service Provider) as well as two additional ones. When set up like in the diagram, this provides complete isolation between the two networks with devices on them. There is a third network here, and that is the one consisting of the three routers. That network is now the WAN (Wide Area Network) side of the two lower routers. Unexpected traffic from here is not allowed to enter either of the two lower networks, thanks to NAT.
But what if the Internet cable/fiber is terminated in your living room (which is quite typical), and you have to set up all these routers there? If you live with people, they may not appreciate the living room looking like a techno dungeon. And you probably wouldn't either. The mess can be reduced somewhat by using the ISP router for the IoT network (provided its wifi has sufficient strength to reach all your devices), and connecting your main router to the ISP router as a client. Now the IoT network is the WAN side of your main router, and the trusted devices on the inside are still invisible to the vicious IoT devices in your home.
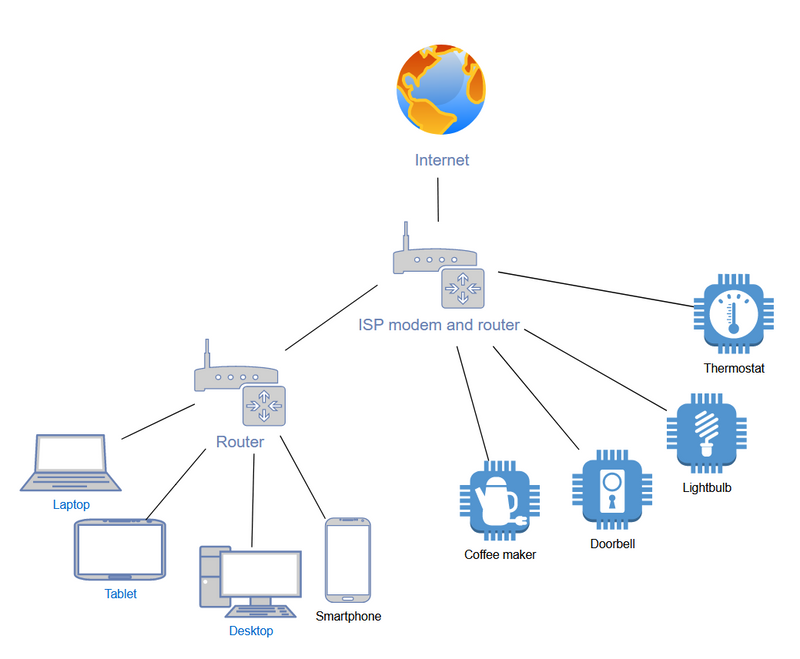
Ok, I know. Two routers in the living room is not great either. Thankfully there is a simpler solution.
Guest network
Many routers provide the option to enable a guest network. When implemented correctly this gives you a second WiFi network with a separate SSID and password. Any devices connected to this network should be isolated from everything on your main network. If the router vendor has done things right, the devices on the guest network should not even be able to see each other. The guest network simply provides its clients with access to the Internet. This is ideal for sharing bandwidth with your guests, whose phones you should probably not trust to be secure enough to enter your main WiFi. It is also ideal for IoT devices which only need access to the Internet, ie. they have no (legitimate) need to talk to any other devices in your house directly. This applies to many IoT devices, which only need to communicate with a remote server, and you get access to monitoring and control capabilities via an app which also communicates with that server.
But what if your devices actually need to talk to each other directly, on the local network? An example could be casting video to a Chromecast device or music to a Spotify-enabled smart speaker. Well, you could just forfeit and put those devices on the main network. But there is another way.
Virtual networks (VLAN)
If you have a VLAN capable router, you can configure multiple virtual networks which run on the same physical infrastructure, whether this infrastructure consists of WiFi, cable or both. It works by attaching VLAN-specific tags to the Layer 2 data frames which are sent around the network. You set up the different VLANs in the router's admin interface, and then specify which VLAN should be attached to each physical Ethernet port on the router's integrated switch, as well as downstream VLAN capable switches connected to the router. You can also set up multiple WiFi SSIDs and attach them to VLANs in a similar manner.
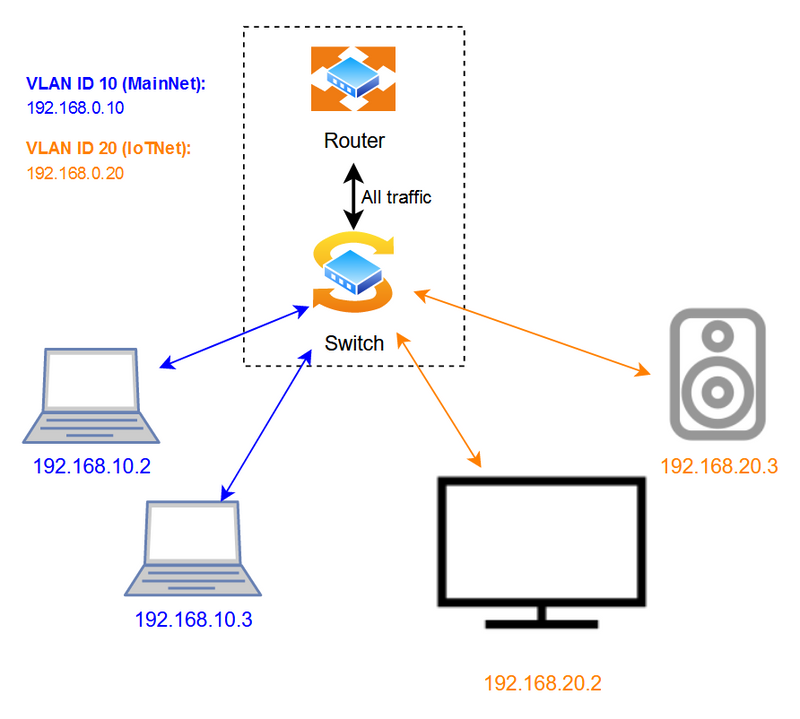
Let's look at an example using physical connections (illustrated in the above diagram). We create two VLANs called MainNet and IoTNet. We enable MainNet on the switch's ports 1 and 2, and IoTNet on ports 3 and 4. Then we connect two computers (by ethernet cable) to ports 1 and 2, and a smart TV and a smart speaker to ports 3 and 4 respectively. Even though these devices are now physically connected to the same switch, the computers cannot see the smart devices, and vice versa. Even if the SmartTV knew the IP address of the PC connected to port 1 and wanted to talk to it, it would not be able to do so directly via the switch. This is because the data frames coming from the TV will be tagged with the IoTNet specific tag when entering port 3 on the switch. These tagged frames are not allowed to traverse port 1, which requires all frames to be tagged with the MainNet specific tag. Since the switch cannot forward this traffic directly to the destination, it is instead sent to the router. Now the firewall rules programmed into the router will decide whether the smart TV on IoTNet should be allowed to talk to the PC on MainNet. You can probably see that this is an extremely flexible approach, which enables strict segmentation as a base, but allows for configuration of exceptions where needed.
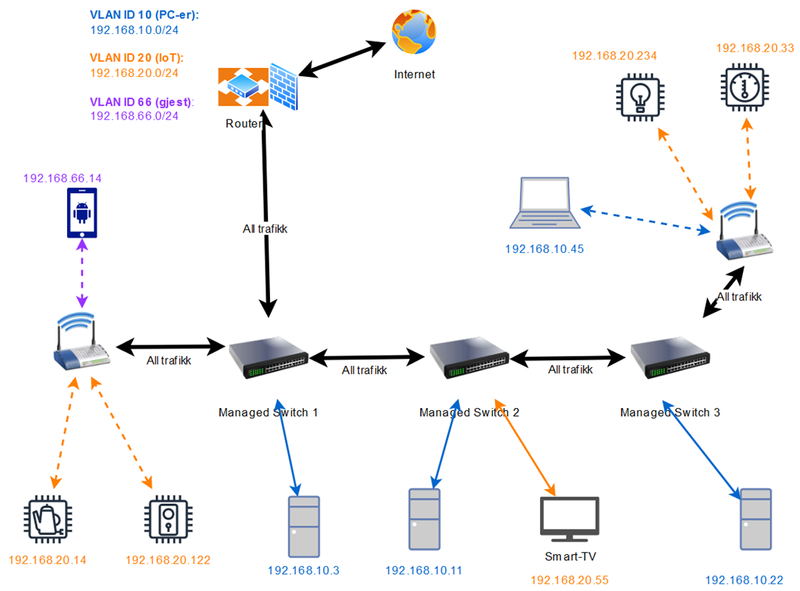
This concept works for small networks as well as large, as you can see in the above diagram. Multiple VLAN programmable switches can be connected to the router, and wireless access points can be connected to provide WiFi. You can create multiple VLANs to separate your devices into smaller groups, further minimizing the risk of a mass network compromise.
If your home network topology is somewhat complex, consisting of a mix of wired and wireless devices scattered throughout the house, then VLANs are the ideal way to make sure each device is only allowed to talk to the stuff it needs to. Note again that you will need a VLAN capable router (which may have an integrated switch and WiFi access point), as well as VLAN enabled switches and access points if you need to expand beyond the connectivity of the router. In this case you will be doing yourself a favor by choosing hardware from a single product line, as the job of configuring it all will be much simpler when all the devices are meant to work together.
Wrapping up
Using a guest network is probably the right solution for most people to significantly decrease the risk associated with rogue IoT devices on the network. VLANs provide more flexibility at the cost of complexity. You decide which approach is right for your network.
Further reading
If you want to learn more about the security and insecurity of your home network, check out some of these resources:
IoT security at home (bekk.christmas 2020)
Essential tips for securing your home network (bekk.christmas 2018), most of which you should probably do before embarking on the wonderful journey of network segmentation.
Routersecurity.org by Michael Horowitz. If you want to really go down the rabbit hole of network security, this is the place.
Up next...
Loading…
Loading…
Loading…
Loading…